How I discovered a homograph attack by mistake…
For many that don’t know, Privnote.com is a website where people can share a confidential note via a web link. The weblink will self-destruct after your intended recipient reads it. This website has been up since July 2008, and it has been used until now by 1.9 million users.
What did I found?
Because the website doesn’t rely on Open-Source code I never trusted it so much (sorry folks…), so I decided to build one and give it to the world (it’s a work in progress for now), however meanwhile I was doing some research I typed on the URL bar of my browser and wrote privnote instead of typing the full address, and the magic happened!
A Google search started, and here you can see, the result of it:
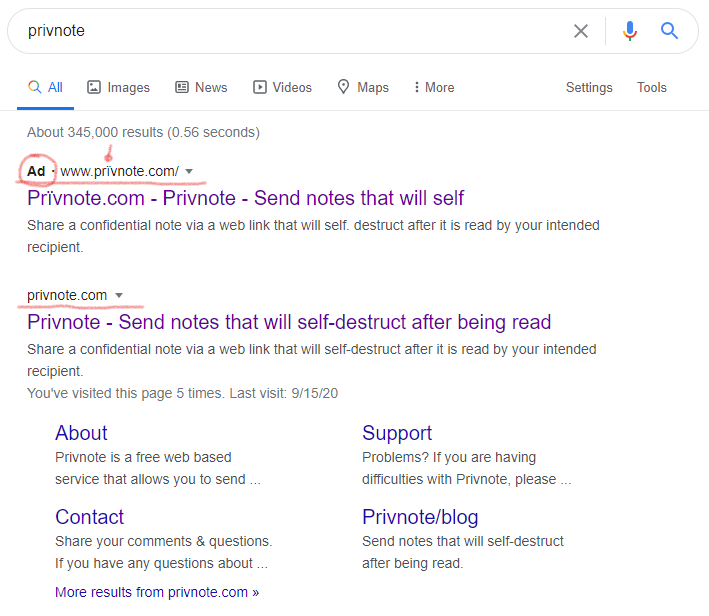
At first look, everything seemed fine, but if you check more carefully, you will notice that Privnote is misspelt as Prïvnote and I thought it was really weird that they used the diaeresis on the advertised link. It was too fishy for me not to have a look at it and deep dive a little bit… So I did some basic analysis first, by retrieving the WHOIS information of both sites.
Here the result of Privnote.com registered on Godaddy:
Domain Name: PRIVNOTE.COM Registry Domain ID: 1256221974_DOMAIN_COM-VRSN Registrar WHOIS Server: whois.godaddy.com Registrar URL: http://www.godaddy.com Updated Date: 2019-10-06T15:59:24Z Creation Date: 2007-10-05T05:26:10Z Registrar Registration Expiration Date: 2020-10-05T05:26:10Z Registrar: GoDaddy.com, LLC Registrar IANA ID: 146 Registrar Abuse Contact Email: abuse@godaddy.com Registrar Abuse Contact Phone: +1.4806242505 Domain Status: clientTransferProhibited http://www.icann.org/epp#clientTransferProhibited Domain Status: clientUpdateProhibited http://www.icann.org/epp#clientUpdateProhibited Domain Status: clientRenewProhibited http://www.icann.org/epp#clientRenewProhibited Domain Status: clientDeleteProhibited http://www.icann.org/epp#clientDeleteProhibited Registrant Organization: Ikatu Registrant State/Province: Registrant Country: UY
Here instead of the result of the second Prïvnote.com registered on 101domain:
Domain Name: XN--PRVNOTE-PZA.COM Registrar WHOIS Server: whois.101domain.com Registrar URL: https://www.101domain.com/ Updated Date: 2020-09-26T01:04:30Z Creation Date: 2020-09-18T09:48:31Z Registrar Registration Expiration Date: 2021-09-18T09:48:31Z Registrar: https://www.101domain.com/ Registrar IANA ID: 1011 Registrar Abuse Contact Email: abuse@101domain.com Registrar Abuse Contact Phone: +1.7604448674 Domain Status: clientTransferProhibited http://www.icann.org/epp#clientTransferProhibited Registrant State/Province: Registrant Country: RU TO CONTACT REGISTRANT, COMPLETE THIS FORM: https://my.101domain.com/contact-registrant/XN--PRVNOTE-PZA.COM.html Name Server: NS1.101DOMAIN.COM Name Server: NS2.101DOMAIN.COM
Wait… What!?!?!
Ok, so now the things are becoming more and more interesting!
The second website is actually a redirection to another domain XN — PRVNOTE-PZA.COM and differently from the original website this domain was bought only a few days ago (Creation Date: 2020–09–18T09:48:31Z), so another question popped in my mind, what about the SSL certificate of those two websites, and again as I thought I had some confirmation because the original website gave me this SSL results:
Common name: privnote.com
SANs: privnote.com, www.privnote.com
Organization: Gletin S.A.
Location: Montevideo, UY
Valid from March 12, 2020 to March 18, 2022
Serial Number: 0672f0f3d240126383a705724487f6df
Signature Algorithm: sha256WithRSAEncryption
Issuer: DigiCert SHA2 Extended Validation Server CA
Meanwhile what we will start calling the Evil Privnote gave me this SSL results:
Common name: xn — prvnote-pza.com
SANs: www.xn--prvnote-pza.com, xn — prvnote-pza.com
Valid from September 19, 2020 to December 18, 2020
Serial Number: 04b5a88a90d4431bbf4c01865f4ddf4f1514
Signature Algorithm: sha256WithRSAEncryption
Issuer: Let’s Encrypt Authority X3
As you probably notice, there isn’t any Organization specified, nor the Location, which doesn’t make any sense for a legit company. In fact, if you look online, we can easily find out that Gletin S.A. which is the company that owns Privnote has also registered the Privnote trademark, so why on Earth a company should open a twin website after years and not even register it under its name?
Unless of course, the second website is a malicious website created by someone else. The last question now is, how can we be sure?
I used a free online sandboxing tool to analyse both links; you can see the published results here:
The original website is fine as I expected, but the second one, unfortunately not:
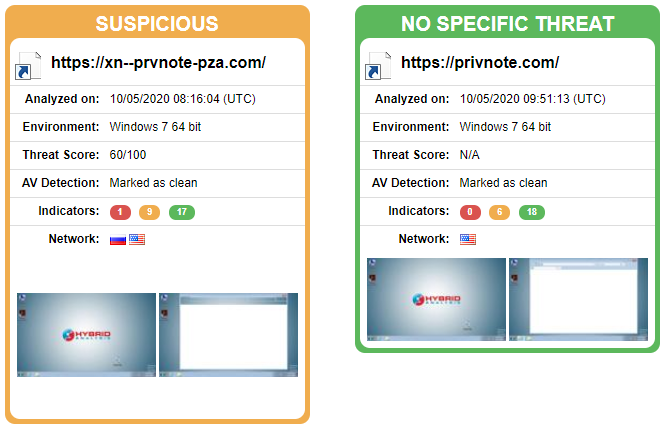
If we then check in detail why an indicator is flagging the website as malicious, we find this:
Detected Suricata Alert
Detected alert “ET PHISHING Lets Encrypt Free SSL Cert Observed with IDN/Punycode Domain — Possible Phishing” (SID: 2024227, Rev: 3, Severity: 1) categorized as “Potential Corporate Privacy Violation”
source Suricata Alerts
relevance10/10
So it seems I discovered a real and alive example of homograph attack, which is well explained here in this article from Wandera.com, where:
the URLs will look legitimate, and the content on the page might appear the same on the face of it but its actually a different website set up to steal the victim’s sensitive data or to infect the user’s device. These attacks use common techniques like phishing, forced downloads, and scams.
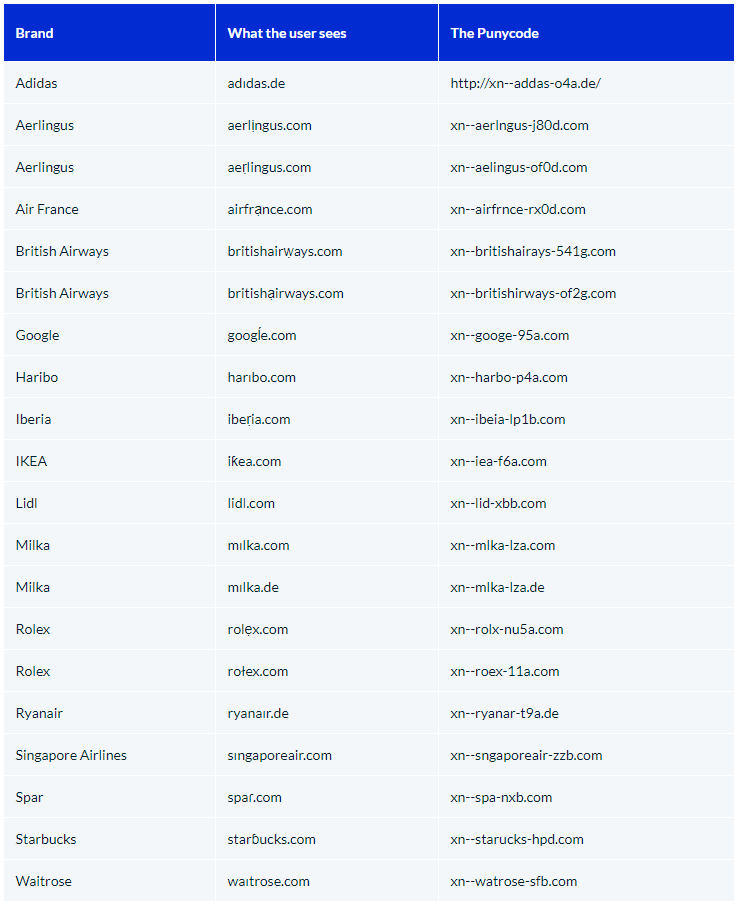
on the same website, we can find a list of other domains found in the past that were using this type of attack that are extremely similar to the one I found:
Conclusions
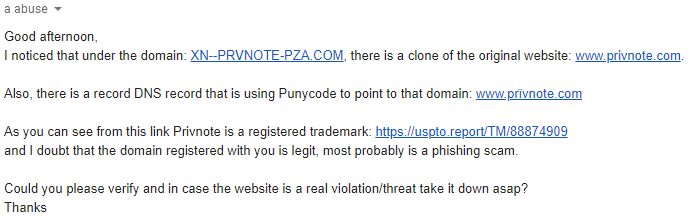
I already sent an email to 101domain asking them to check and possibly shut-down the website as soon as they can, and I also informed Gletin S.A. that someone cloned their website and used their registered trademark for a phishing attempt.
This situation poses some doubts, first, how is even possible that Google is allowing a phishing website to be advertised on their pages considering that the original one has a trademark registered? How can companies protect their websites? And secondly, if this is the situation what can users do to prevent it?
Although I would like to answer every question I don’t have an answer for the first one, for the others, there are services online that companies can use to be sure that their domain will be reserved and that diaeresis will not be used, or services to check plagiarism online to avoid other people from recreating a similar website.
For the users, there is no shortcut; unfortunately, the only way is being careful, read articles like this and stay always informed and updated on end-user security. I could give a long list of precautions you should take, but you will end up following it without understanding why and the risks that you will still be exposed to.
Stay informed but mostly stay alert!